BACE (Build a Connection Everywhere) is the product line created by EVALAN to help anyone digitalize their assets and build state-of-the-art Internet of Things (IoT) applications quickly.
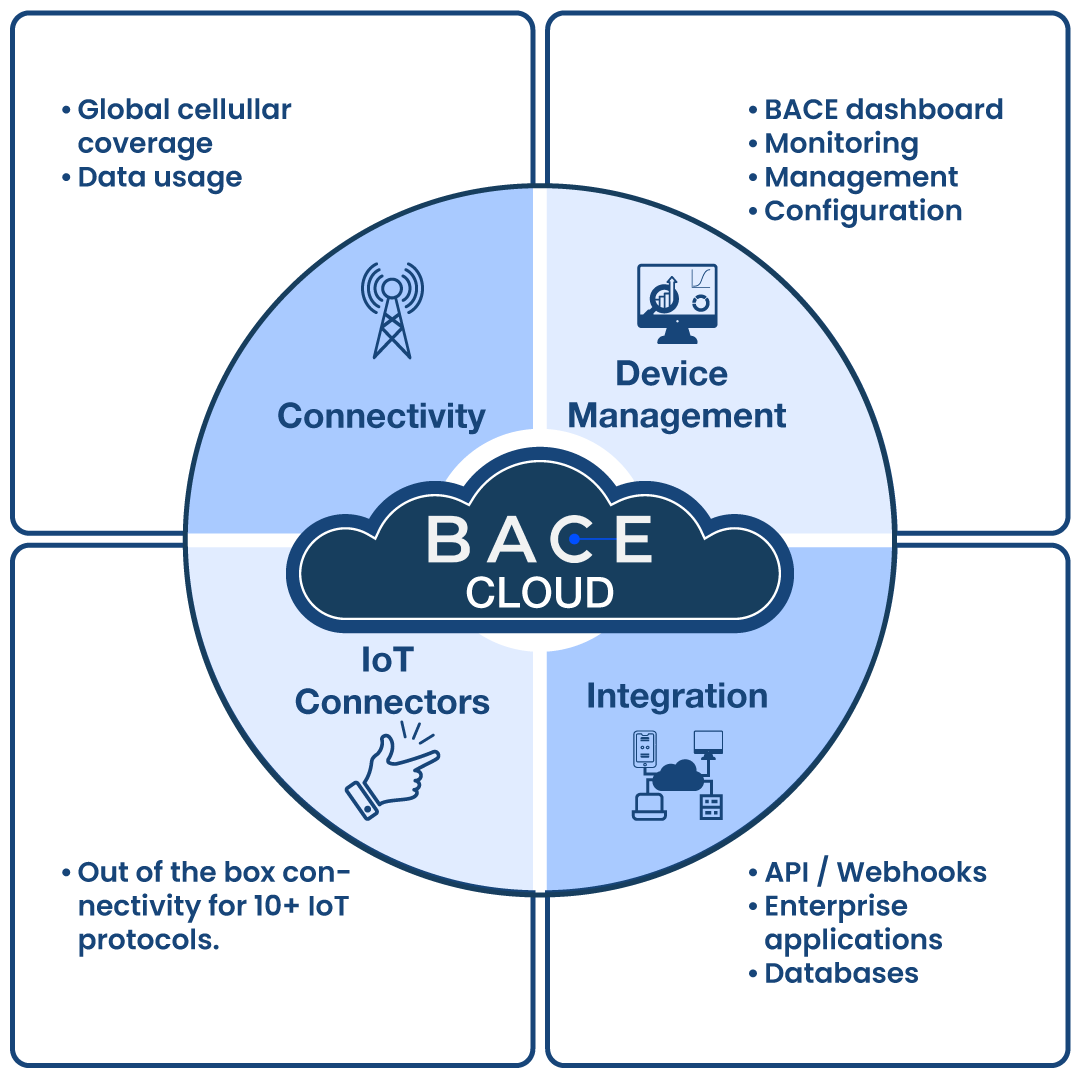
BACE has two highly integrated parts: the BACE gateway and the BACE Cloud, a PaaS (Platform as a Service) that provides four pillar services and combines several applications to help you build your IoT solution without having to worry about building and maintaining the underlying infrastructure.
The BACE PaaS as a private deployment
The standard BACE platform is hosted on a shared cloud resource with other tenants and EVALAN takes care of all operations related to the infrastructure, maintenance, scaling and security.
We are aware that companies in some industries need to follow specific privacy and security regulations. For them, we offer the flexibility to run a private instance of BACE platform under their own Microsoft Azure account. This provides them with full control of anything happening in the system, with our guarantee of:
- Smooth operations and a maintenance free data pipeline.
- Easy configurability when changes are needed, or devices/users need to be added.
- Optional operational services for keeping devices up to date and running.
More on Security
Because the security of an IoT deployment depends on the protection of all its components, we implement security from the design stage at device and cloud level and pay special attention to privacy.
Security at the Gateway level
1. Flash Encryption
First, during the assembly process, the BACE gateways are protected with flash encryption, which helps keep the data stored on the device safe from unauthorized access or tampering. Each gateway has its own unique key for encrypting and decrypting stored data on the microcontroller, which cannot be accessed by any third party.
2. Firmware Encryption
Second, the firmware running on the gateway is also encrypted which makes it difficult for anyone to see how the firmware works or to access any sensitive information that it may hold.
3. Secure Boot
Third, to prevent malicious software or firmware from being installed on the device, the BACE gateways do secure boots. This feature prevents unauthorized firmware from running on a gateway manufactured by EVALAN, and hence helps to avert cyber-attacks and other security breaches.
4. Identity Certificate
Fourth, to connect with the BACE Cloud, each gateway includes a specific identity certificate which gets verified and authenticated every time a communication to the Cloud platform occurs. Furthermore, the communication between the device and Cloud is also encrypted.
Related to the last point, is the fact that we also support encryption for wireless communication (e.g., Z-Wave and Wi-Fi) with third party devices that support it; this is especially needed when sending sensitive information, for example in healthcare.
Security at Cloud level
The security at the Cloud level is divided by design into several layers, including separate security for the data in transit and for the data in rest. For the former, when information is sent from one system to another, the information is encrypted following several protocols.
For the latter, we implement secure passwords, roles and permissions, which means that access to data is done through accounts and granted based on roles and functionalities that specific users need. Furthermore, the information is isolated and kept in a private network.
In that sense, if a breach occurs, only data in transit is visible, thus limiting the attack surface.
Privacy by design
Finally, it is important to note that our systems always consider the sensitivity of data and do not store or send personal information. In that sense, we follow the subsequent principles to ensure privacy and compliance to the GDPR:
- Purpose limitation: we collect data only if it’s used for processing (the processing purposes are specified in our privacy policy).
- Data minimization: we only collect the necessary amount of data for the service.
- Storage limitation: we offer automatic retention of data based on a custom retention period.
- Integrity and confidentiality: the data is stored securely and confidentially in our private databases.
- Transparency: EVALAN is open and clear about all security and privacy principles applied in its IoT solutions.
Want to know more?
- Send us an email to info@evalan.com
- Or book a meeting with us here: